Self-Sovereign Identity: A New Approach to Digital Identity
June 12th, 2023Most users are familiar with current Digital Identity models: centralized and federated identity verification. Centralized identity consists of creating logins and passwords that are stored in a central database. This model has presented problems with both security and usability because it requires users to create login credentials and passwords, making it difficult to manage and prone to theft. Federated identity involves sharing personal data with a 3rd party for verification, which users may not trust. Today’s digital identity models leave a lot to be desired in terms of user experience and security.
However, a new approach for Digital Identity has emerged with promising potential. Self-Sovereign Identity (SSI) is a digital identity approach that supports peer-to-peer verification of personal identity. SSI is made up of two components: Verifiable Credentials (VCs) and Decentralized Identifiers (DID).
Verifiable Credentials are tamper-proof credentials whose authorship can be cryptographically verified.
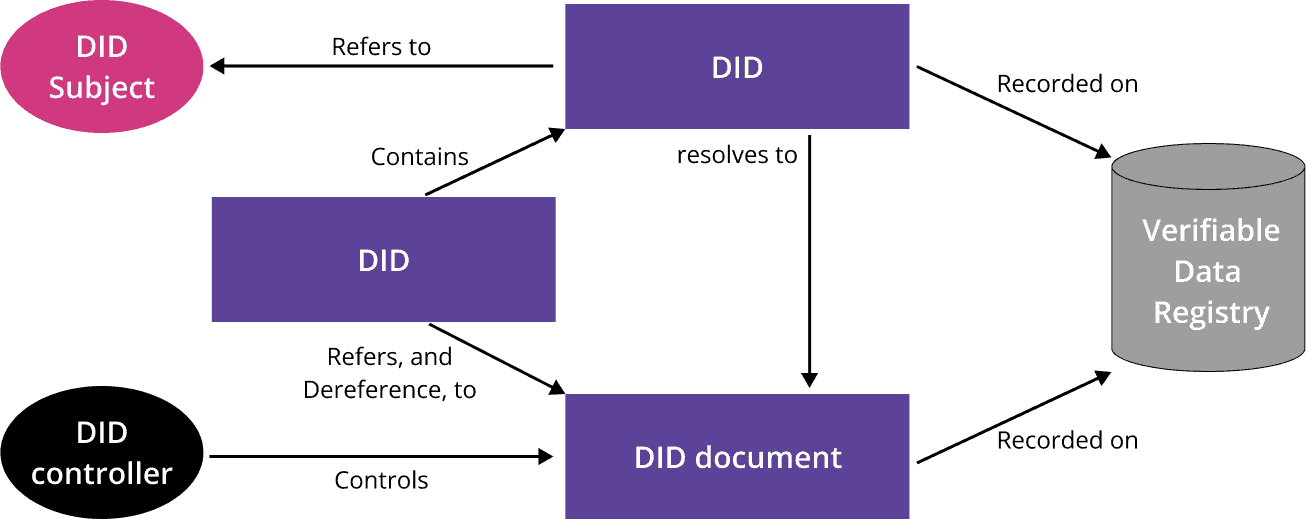
Decentralized Identifiers are unique, global identifiers that do not require centralized registration authority, but instead are generated and verified cryptographically. A DID document is a document that is accessible using a verifiable data registry and contains information related to a specific decentralized identifier, such as the associated repository and public key information.
The basic workflow of a Self-Sovereign Identity solution is:
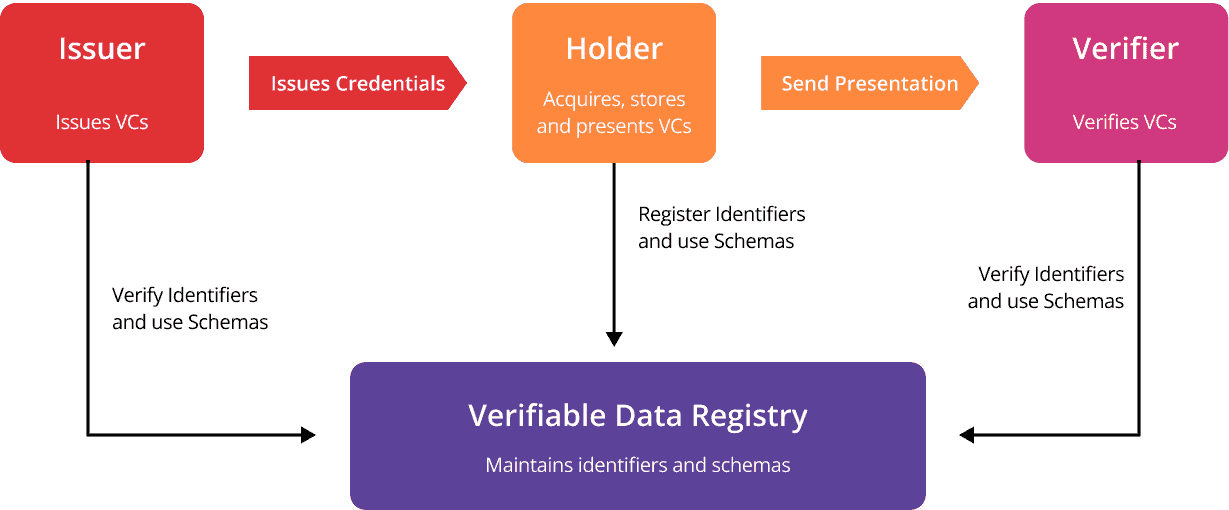
- There are three main actors: Issuer, Holder, and Verifier.
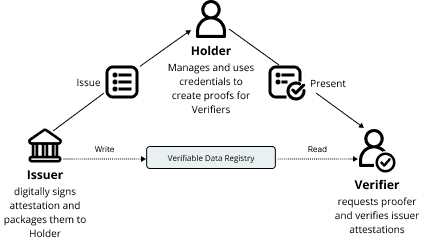
- The issuer digitally signs and issues verifiable credentials (VCs) to a holder, or manager of the credentials. The verifiable credential is signed by a key associated with the Issuer’s DID.
- Issuer’s DID and corresponding public keys are put into a verifiable data registry (VDR), usually a public distributed ledger or blockchain, such as Hyperledger Indy-based ledger or cheqd. Moreover, the credential is usually associated with the Holder by using the Holder’s DID as a subject. Holders have the option to use peer/pairwise Identifiers instead of ones from public VDRs (such as distributed ledgers).Some types of verifiable credentials (such as CL Anoncreds) bind the credential to a Holder via a so-called linked secret.
- The holder stores the VCs locally, usually in a Mobile Wallet. Please note, that VCs are never put into a verifiable data registry or blockchain. The holder of these VCs can now present them to a verifier. The presentation may contain multiple VCs and usually contains proof of VC ownership by the Holder, such as a signature based on the linked secret or the keys associated with the Holder’s DID that was part of the VC subject.
- Verifier checks the validity of the presentation by verifying the signatures.
Some impactful uses of Self-Sovereign Identity are proof of identity and proof of ownership. SSI can help a store owner verify the age of a buyer, allow employers to certify resumes, and let someone prove their employment while applying for a loan. In almost all cases where certain information must be verified before a future action can be taken, Self-Sovereign Identity can be implemented.
There are applicable use cases for Self-Sovereign Identity across industries, including governments, healthcare systems, finance, and tech.
- Governments and Municipalities can use Self-Sovereign Identity for digital IDs, passports, business certificates, and establishing proof-of-ownership.
- Healthcare organizations can keep a verified account of a patient’s medical records, prescriptions, and vaccinations, which can be securely shared with a patient and other hospitals or clinics.
- Bankers and Finance professionals can utilize SSI for authenticating transactions, simplifying KYC procedures, and verifying loan applications.
- Manufacturing and tech professionals can authenticate device provenance and authorship
Distributed Ledgers and Blockchain are optional for Self-Sovereign Identity implementations. The Issuer’s DID, public keys, revocation registries, and credential schemas are usually stored on a public distributed ledger or blockchain, though they can be stored in other trusted (including centralized) verifiable data registries. The Holder’s DID and public keys can be optionally stored on a public distributed ledger, though in many cases peer/pairwise identifiers and keys are enough. Verifiable Credentials and private keys are never stored on the blockchain.
Digital Identity is only becoming more prevalent in today’s world. Current digital identity frameworks have shortcomings in terms of security and user experience. Self-Sovereign Identity is a new digital identity approach that allows entities to verify digital information presented to one another using tamper-proof and verifiable credentials. The market uses of SSI can be applied to any interaction where credentials need to be verified. Self-Sovereign Identity puts control of personal information back into the hands of the user while allowing entities to securely verify information and credentials.
To learn more about DSR’s SSI solutions and use cases, please visit: https://en.dsr-corporation.com/technology#blockchain